


Recently, we went into some of the hows and whys of OpSec, and discussed a few tools & resources that you can utilize in order to better protect your assets & privacy. This week, I’ll be focusing on one specific platform, as I’ve found their collected information to be incredibly helpful when it comes to performing due diligence prior to investment, or following up on rugs & exploits after they’ve happened.

The platform is DefiYield, and while they have their own value proposition & use-case for potential investors – I’m much more interested in the free tools & databases available to anyone. Specifically, I want to look at the audit database and rekt database, although the approval tools & impermanent loss calculator might also be worth a look.

When investing in crypto assets, you generally want to make sure that an audit has been performed by a reputable & experienced company, and is publicly available. This is to limit potential risk of rugs, exploits, and centralization of privileges. Please note that I said limit, not remove.
Most auditors are going by checklists of common issues & exploits, and making sure the contract doesn’t have any, or advising teams on corrective actions if some are found.
Using the audit database you can sort by project name, issues, auditor, and so on. With some 3,700+ audits linked, it is a much easier way of quickly viewing & comparing projects & audits than by searching a project or auditor’s website, one-at-a-time.
Audits vary wildly from auditor to auditor, with some doing deep examination of potential centralization issues, and some mostly looking for exploits. What they all tend to have in common, though, is a severity ranking of issues from Critical all the way down to Low, or Stylistic/Efficiency issues.
What you’ll want to check is that projects either have the Critical & Major issues resolved (and hopefully the medium severity ones, as well), or at least to have a rock-solid explanation of why they don’t need to be. Sometimes there is a good excuse, if they are still in the process of auditing & adjusting, then they may not have renounced ownership or associated privileges.
Usually, though, you’ll want to see these issues resolved in a timely fashion, as they generally represent associated risks. “What kind of risks?”, you ask? For that we’ll want to check the…
The REKT Database examines the other end of the spectrum. Whereas audits are a pre-investment derisker, the rekt database is a post-mortem of when things have already gone from bad to worse.
The main page will give you a quick glimpse at the most recent reports added to the database, as well as nauseating stats on funds lost vs. recovered, and a chart to demonstrate the progression of both over time.
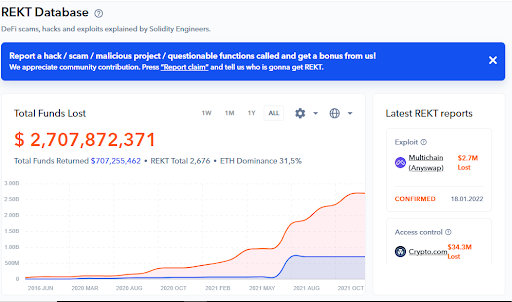
The optional filters & sort-by options in the database can be incredibly helpful, too, as you can not only sort by the type of event or attack, auditors, chains, dates, or total funds lost.
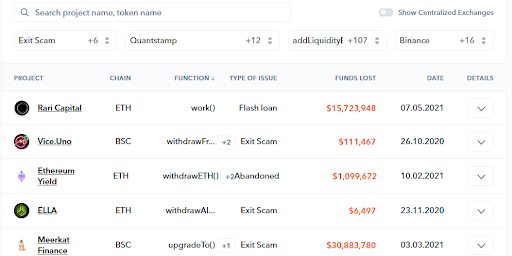
Even better, if you go into the details, you can usually find the timeline of events, related tweets, attackers’ addresses, and more. Essentially, you can see the “history” of a multitude of attacks, exploits, and exit scams, and go as deep down those rabbit holes as you please.
I encourage you to play around with this database, and then use your findings to help fill out the information you find in audits. There are a lot of ways that you could approach this, such as comparing the total # of audits that an auditor has in the audit database with the number of attacks after an audit.
Additionally you could compare the most-used attack vectors & functions to the issues remaining in audited contracts. Do you see upgradeTo() being a common component in attacks & exit scams? Well, that might be something to consider if an audited contract retains access to that function.
Having the ability to easily compare these things is fantastic, although I will say that with newer projects you’ll likely still have to find the audit via the project or auditor’s website. DeFi Yield also performs their own audits, so be aware of the possibility that rekt reports added to the database may be skewed to paint their audits more favorably than competitors.
I haven’t seen evidence of that, personally, but you always want to consider bias & motivations involved, or potential conflicts that may arise because of them.
This is by no means an all-inclusive resource, either, but it is a handy bookmark to have in your fundamental analysis toolkit, and reading audits & post-mortems is a great way of increasing your understanding of contract functions & potential threats. As I mentioned last time, keeping an eye on your approvals & allowances is also a good idea. The approved contracts tool I mentioned before is another great way of doing that.
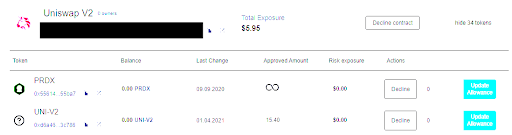
One thing I really like is that they break down each approval/allowance & show your associated risk in $ for each. I’d imagine this would be very handy for folks when determining which approvals are most worth revoking in terms of risk vs. cost.
Until next time, give these tools a try, and if you find them useful: bookmark. It’s always good to have a folder full of platforms you can utilize when checking out potential investments.

Torrent/seedbox aficionado, decentralist, cultural archivist, fundamental analyst, podcast addict, shitcoin-sifter extraordinaire
Tip Jar
BTC: bc1qahxrp47hpguhx8y8r382dekgca34tlv54aufht
Doge: DJRy9gGSUGeyXfVcZXzKLkBv7RmDLv3MhJ
Share This Article
Join 10,000+ forward thinkers! Get crypto education in your inbox.