


Let me be clear on one thing: the people trying to take your money are innovating every single day, in every single way. You can’t blame the victims in these hacks or exploits, unless they’re just willfully ignorant. That was not the case, here.
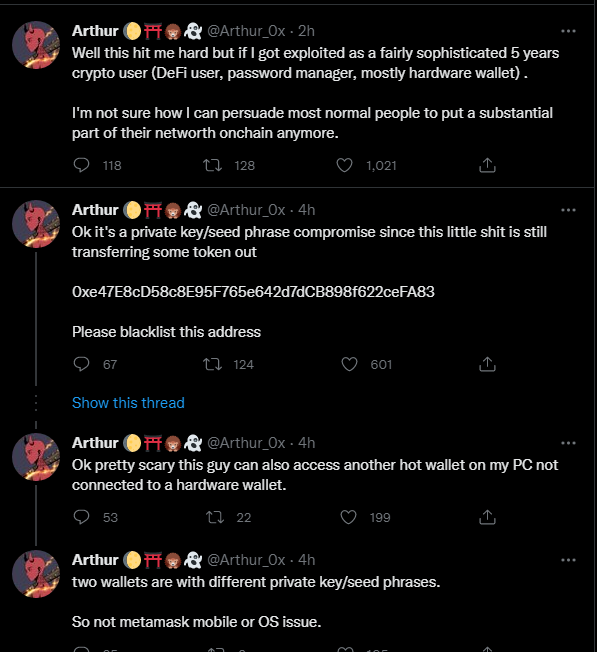
Arthur is the founder of a crypto investment firm, and no stranger to the space or the dangers inherent to it. When he found his NFT wallets compromised, he didn’t just throw his hands up in the air & call it a loss.
He knew different steps to take, what to watch, and a few of the likeliest culprits. He started trying to trace where he might have been exposed. This is the right thing to do; knowing what is exposed & at risk is the first step to saving what you can, if anything.
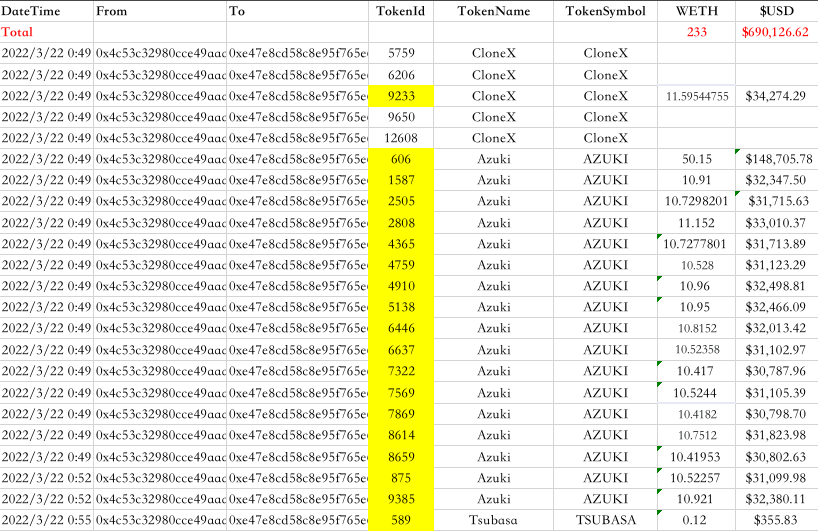
Source: @PeckShieldAlert
Arthur lost over half a million dollars’ worth of NFTs, with a lot of them being immediately listed for cheap & purchased by community members who offered to sell back at cost – I’m not interested in any of that. There are plenty of services that keep track of how much money has been lost to hackers. I’m much more interested in the “how”, and the “how to avoid”.
The “How” requires a quick definition. If you aren’t familiar with them, pitch decks are essentially a flashier version of a whitepaper or litepaper. They’re much more focused on selling the points that projects think investors are most interested in, and they’re also sent to influencers and marketing agencies that might consider working with the project.
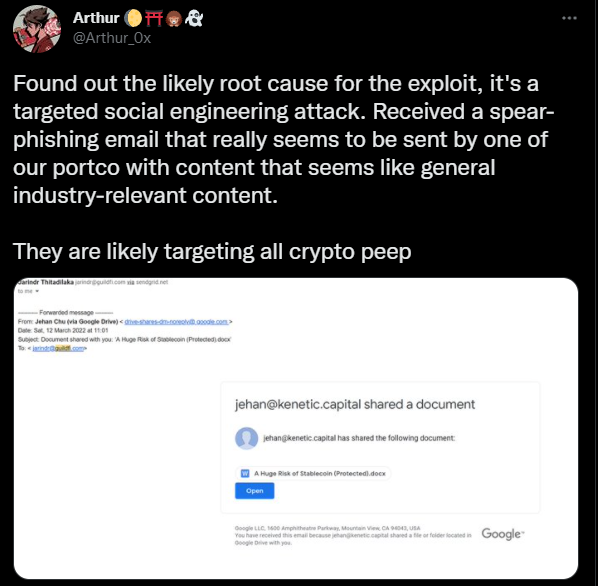
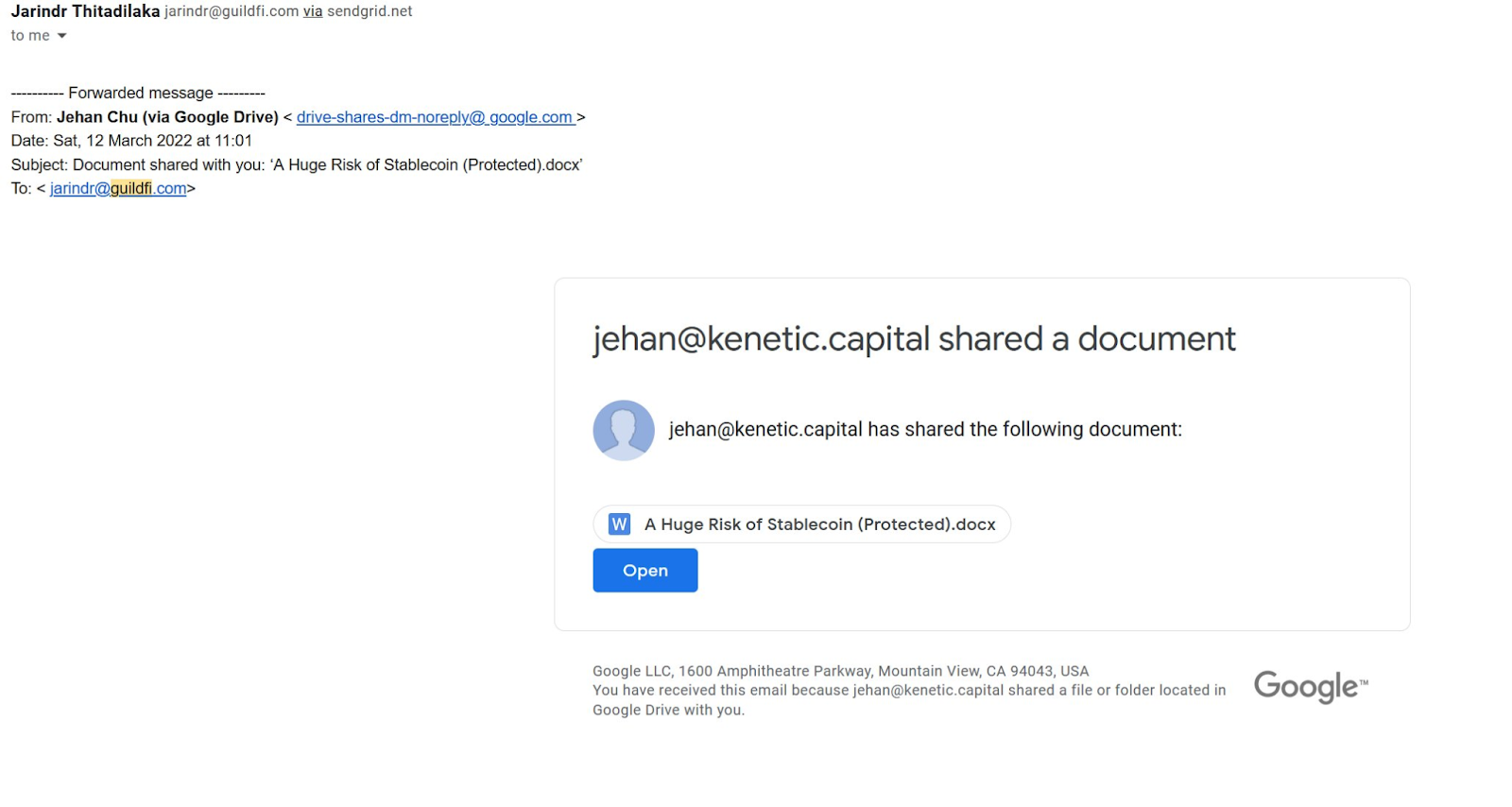
As it happens, I’ve had some friends who work in the industry reach out recently and ask for advice on how to scan for maldocs, as they were receiving so many .docx and .pdf files in addition to all of the demos.
Demos, they were used to. You just toss them in VirusTotal and you’ve got answers within minutes. Who knows, that might have even worked here, if the file had been scanned. Pdf and doc files, though? I mean…what’s in a doc?
As it turns out, potentially a lot. A Georgia Institute of Technology study began compiling instances of targeted attacks using malicious pdf files, adobe components, powerpoint, and others in an attempt to compare the evolution of attacks to the evolution of scanning.
2017 saw a huge spike in these types of attacks, and with the recent boom pushing large amounts of capital into NFT projects, it’s honestly surprising we haven’t had more of these pop up, already. So what do we do about it?
Ideally, you should be opening files from untrusted sources in a sandboxed environment, yes, like Virustotal, or Hybrid-Analysis. There are also better, more time-consuming options like Cuckoo Sandbox.
Personally, I prefer the scanner from Ty Labs in addition to the above options. This is a hosted version of the open source Quicksand project you can find at the linked github.
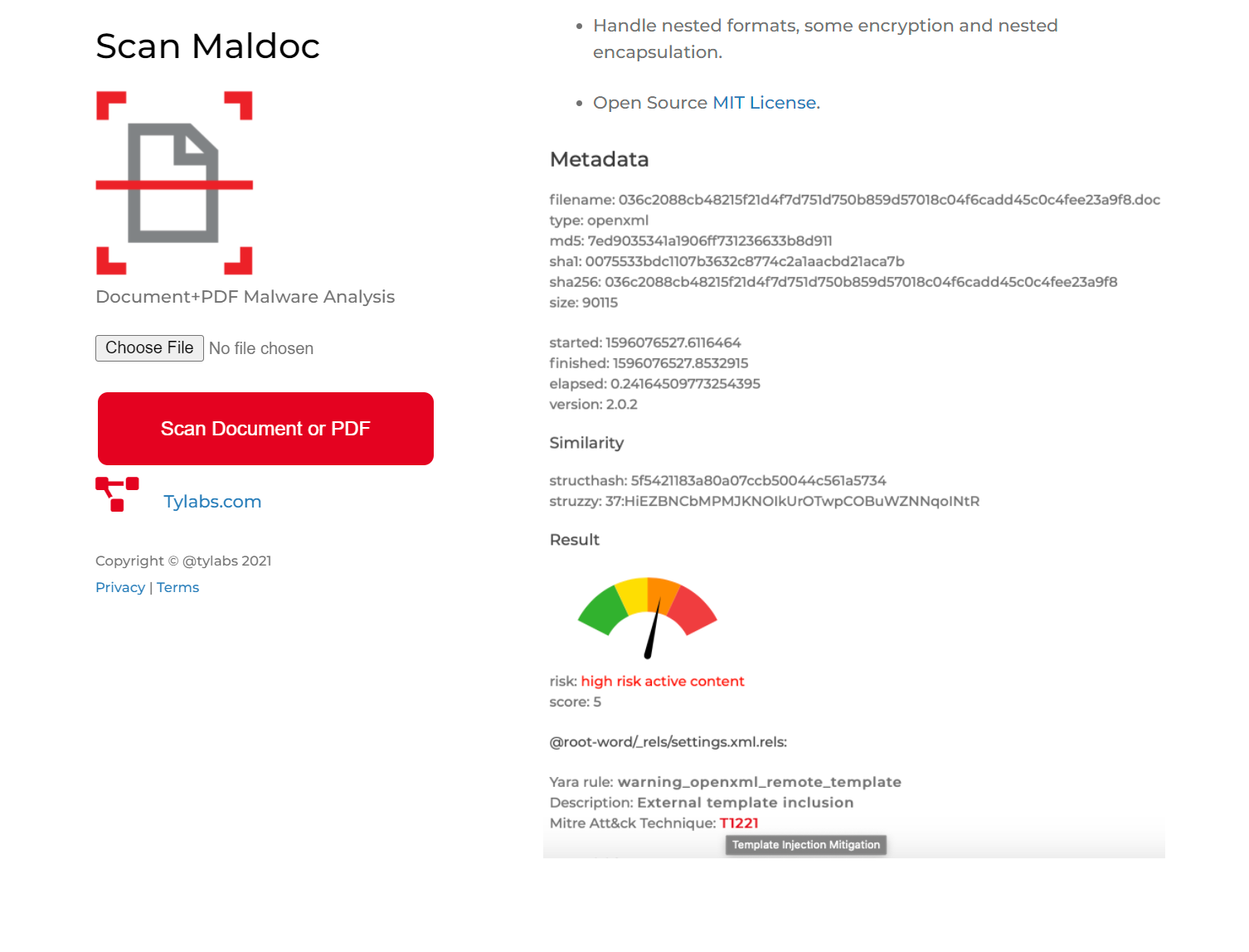
It works basically like virustotal or any of the other sandbox options, but is fine-tuned to scan for the most common activity you see from malicious documents.
The most important thing to remember, though, is to scan even the things you believe came from a trusted source. Remember, this is a trustless space, and it doesn’t work when you trust more.
It is going to become more and more important for VCs, celebrities, and marketers to be just as cautious as crypto-native investors. The stakes are too high, and if your scanning methods aren’t evolving on a daily basis, I can assure you: their attack methods are.

Torrent/seedbox aficionado, decentralist, cultural archivist, fundamental analyst, podcast addict, shitcoin-sifter extraordinaire
Tip Jar
BTC: bc1qahxrp47hpguhx8y8r382dekgca34tlv54aufht
Doge: DJRy9gGSUGeyXfVcZXzKLkBv7RmDLv3MhJ
Share This Article
Join 10,000+ forward thinkers! Get crypto education in your inbox.