


In last week’s article, we discussed how scammers & hackers in crypto are constantly innovating & improving their attack methods, and then we went over some tools for scanning files & documents.
This week, I wanted to dive into another actual attack method that has been plaguing Twitter, recently, and likely has counterparts on other social media networks. On Twitter, specifically, verified accounts are the concern. Historically, these were for celebrities, politicians, or anyone who was a public enough figure that they might be impersonated.
More recently, scammers have been accumulating small armies of verified Twitter accounts & large follower accounts/botnets in order to do concentrated pushes of scams. These accounts can be purchased on several marketplaces, and for less money than you might imagine.
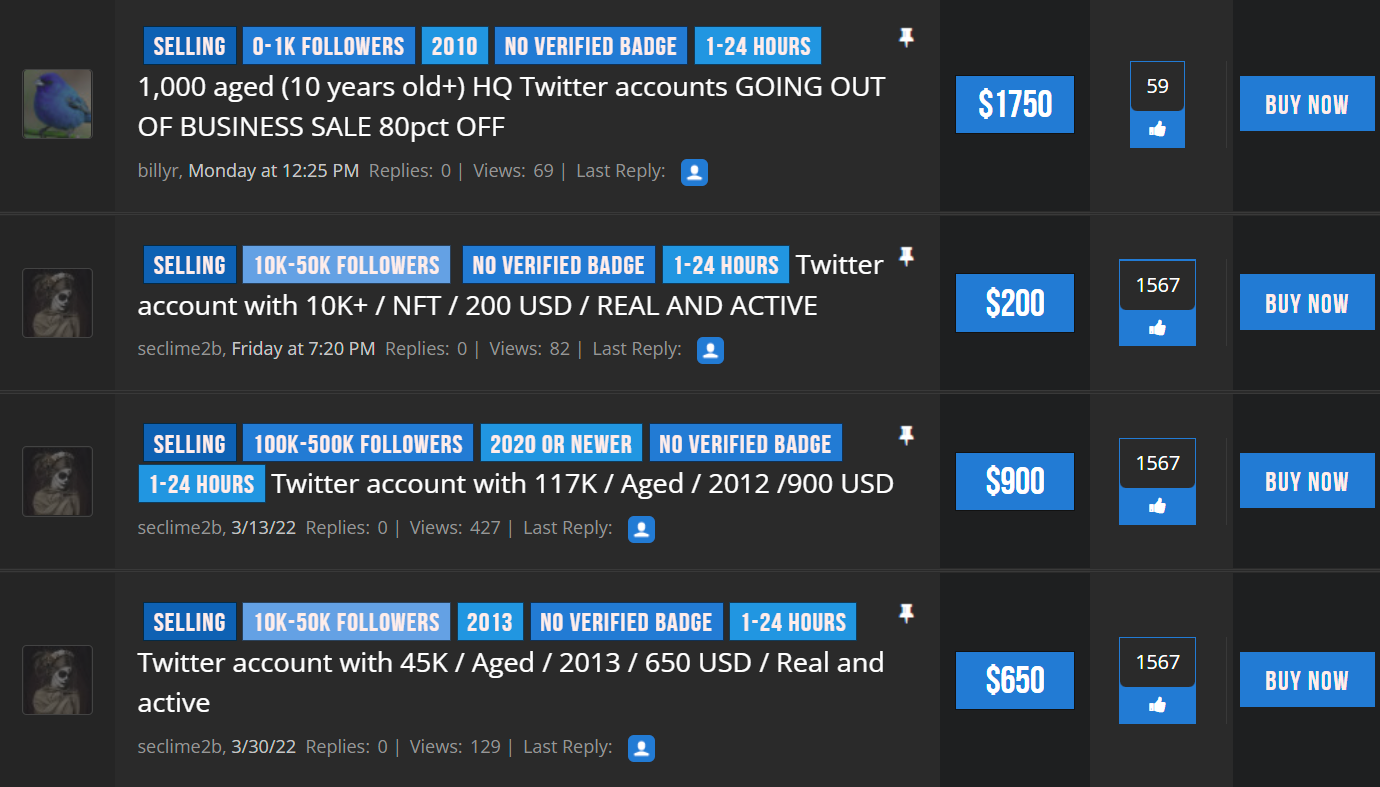
This is why you can’t just look at follower count or account age, in crypto, because I can tell you just by virtue of being here through a couple of cycles; not even half of the large “NFT influencer” accounts had anything to do with crypto a year or so ago.
There are 40,000 follower accounts who just heard about crypto when Top Shot launched, or after some other hype spike. Hell, they might have just heard about it yesterday and purchased a large account then & there. Conversely, most of the smartest people in the space have under 5k followers. When you can spend $200 & be seen as an “expert”, the metric loses any usefulness it might have had.
Crypto Critics Corner did an episode way back in February about the surge in verified accounts shilling questionable links, and it has only gotten worse since then.
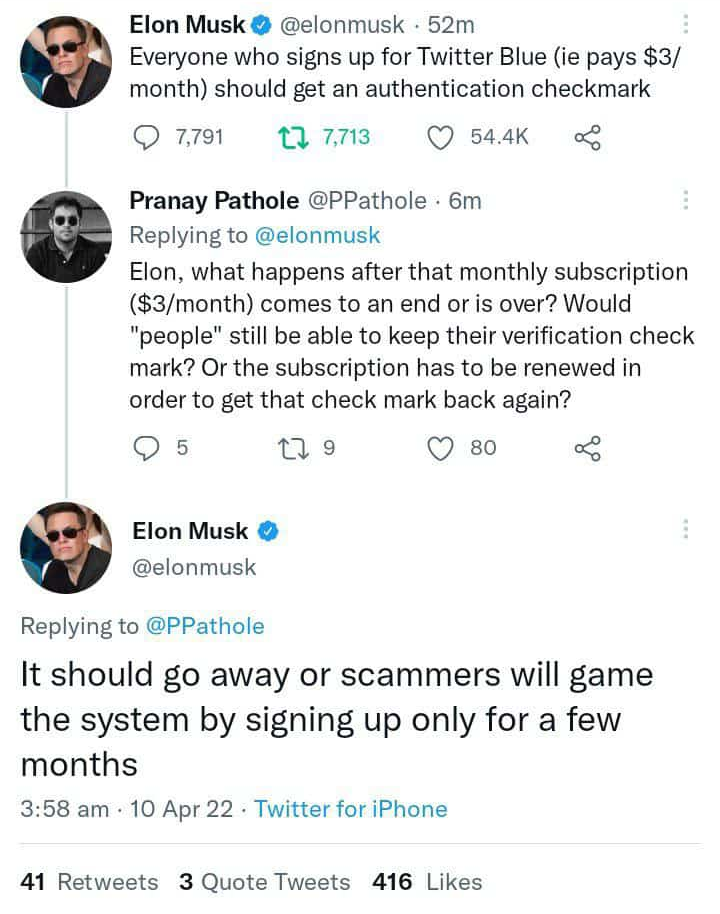
One idea proposed by Elon Musk would have Twitter Blue subscribers all receive a verified checkmark, which would certainly make things worse in the short-term. Long-term, I imagine that this would only lower the perceived value of a checkmark, rendering it sort of pointless overall & largely useless to scammers or anyone else.
Elon even tangentially related the problem to be more about “scammers only paying for a month”, rather than scammers using it at all. Because they absolutely will use it, and they already are.
Currently, the problem is that verified accounts do still carry an air of perceived authenticity, which means unwary users may place some faith in them despite knowing absolutely nothing about them. Even if you don’t know the celebrity or rapper shilling this mint, it might reasonably seem like a catalyst for success.
The sheer volume of scams on Twitter means that even if support staff is on the ball & folks are reporting these accounts as quickly as they pop up, they still likely have a solid 4-8 hour window before the tweets are removed.
This is where the actual gambit begins.
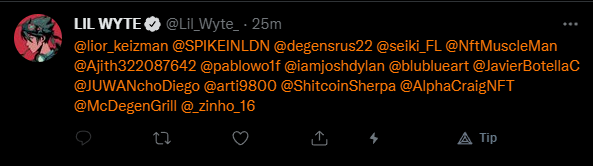
The verified botnets are usually pulling from a list of crypto-facing Twitter accounts they’ve collected from giveaway tags & the like, and they tag as many of them as they can from each of the verified accounts. This helps them catch eyes & concentrate focus in a short timeframe, so they can get as much mileage from the websites & accounts as possible before they’re suspended or blocked.
More importantly, they flag the original tweet as “only tagged may reply”, and tag everyone from a second tweet. This way, no one is able to comment & warn people about the threat. One thing I can say for them: they know how to exploit the mechanics of Twitter to their advantage.
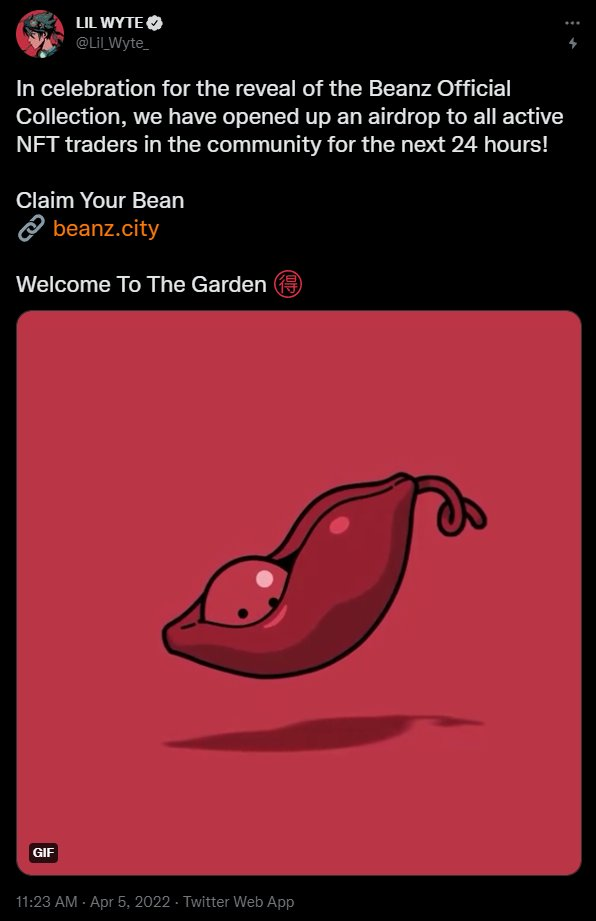
Above you’ll see the actual tweet, but I can’t stress enough that you shouldn’t visit the website unless you’re 100% confident in what you’re doing. I have already archived it for future dissection using the Wayback Machine.
You also shouldn’t think that they all look like this, as I’ve been tagged in several more (including a fake Clonex mint). I kept quoting with a reply warning people about the scam, though, so it looks like I’ve been blocked and removed from the master list.
Upon visiting the website, it looks almost exactly like whatever recent mint it is pretending to be. This is for good reason, as they’ve 1:1 cloned the website & injected their malicious code into it, replacing the original contract mechanics. This isn’t even hard to do, so don’t put the “hackers” up on a pedestal – one thing that should become increasingly more clear as we go along is that most of these scammers are just script kiddies.
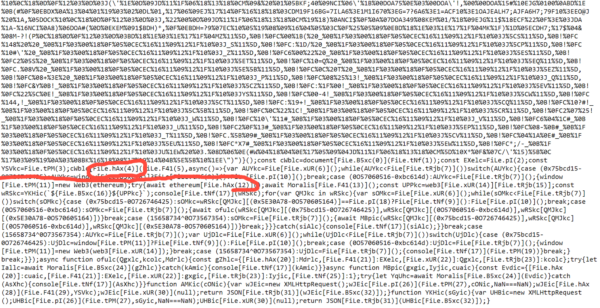
In fact, while I was checking out the javascript used to facilitate this attack, I noticed the coder’s telegram handle commented right at the top. Sure enough, this is a full-time job for the only person involved who knows what they’re doing.
Crickets notwithstanding, let’s get back to the website & what’s going on. When you connect to the website your wallet will request approval to give the website view access to your account. This is pretty normal, right? Totally. Except that once it has view access, some javascript on the site scans your NFTs & holdings to find out what your most liquid & valuable NFTs are, and compiles them in a document unironically titled “file.hAx”.
This is then pulled behind the scenes & the contract pops up a “Safe Transfer Request” (misleading name, yeah?) that needs your approval. To be extra safe, I connected from an illiquid account that couldn’t even afford the gas to be compromised. Sometimes it pays to be poor.
I was never at risk, honestly, because I was expecting malicious requests, and knew well-enough not to approve them. In most cases, “hackers” are depending on you to be in the throes of FOMO and inattentive to the risks. You can generally foil them by slowing down; that’s it – just slow the hell down.
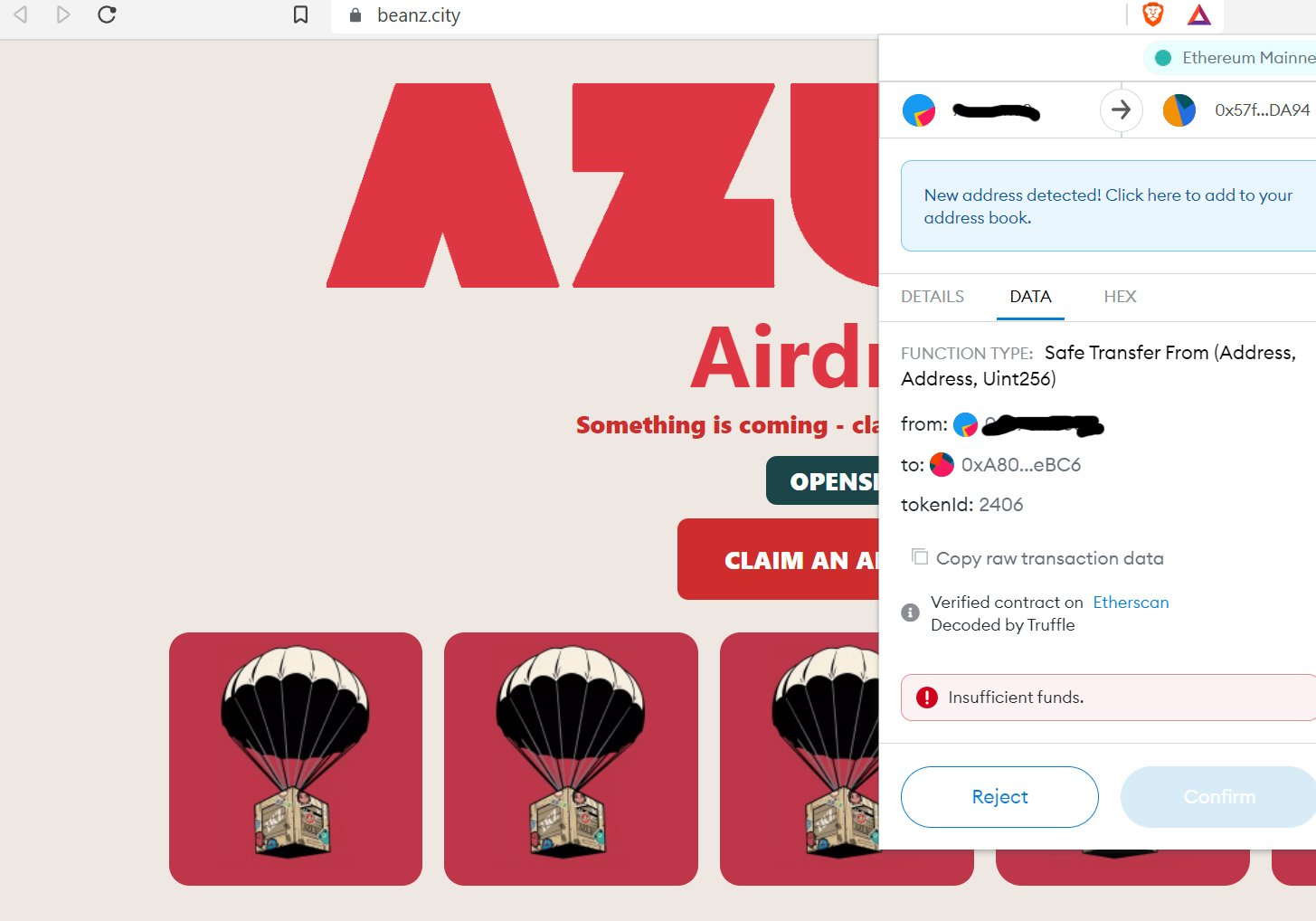
Let’s look a little closer at what they’re doing, though, and how you can tell. The site will actually pop up as many NFT transfer requests as the code deems profitable to steal, so I had to manually disconnect metamask from the site in order to stop them.
When the approval request pops up, we want to tab over to where it says “DATA”. The first clue you should see is that it is in fact a token transfer from you, to them.
The listed tokenId may not be one you recognize, because this is a NFT and you likely won’t be familiar with it, but if you look to where it says “Verified contract on Etherscan”, the Etherscan portion is actually a clickable link to the token’s contract.
Checking this, I knew immediately that they were trying to steal one of my original VNFTs that you might remember from my article on Fair Launches & Forward-Thinking. Not on my watch. Request rejected, metamask disconnected. It really is that simple.
Speaking of “simple”, the attacker uses a simple relay of addresses before sending everything to Tornado Cash & mixing out to a clean address. The thing is, they’re using the same relay of addresses for most of these scams, so you can see one of them I traced still sending out batches 100eth at a time as recently as seven hours before I wrote this sentence.
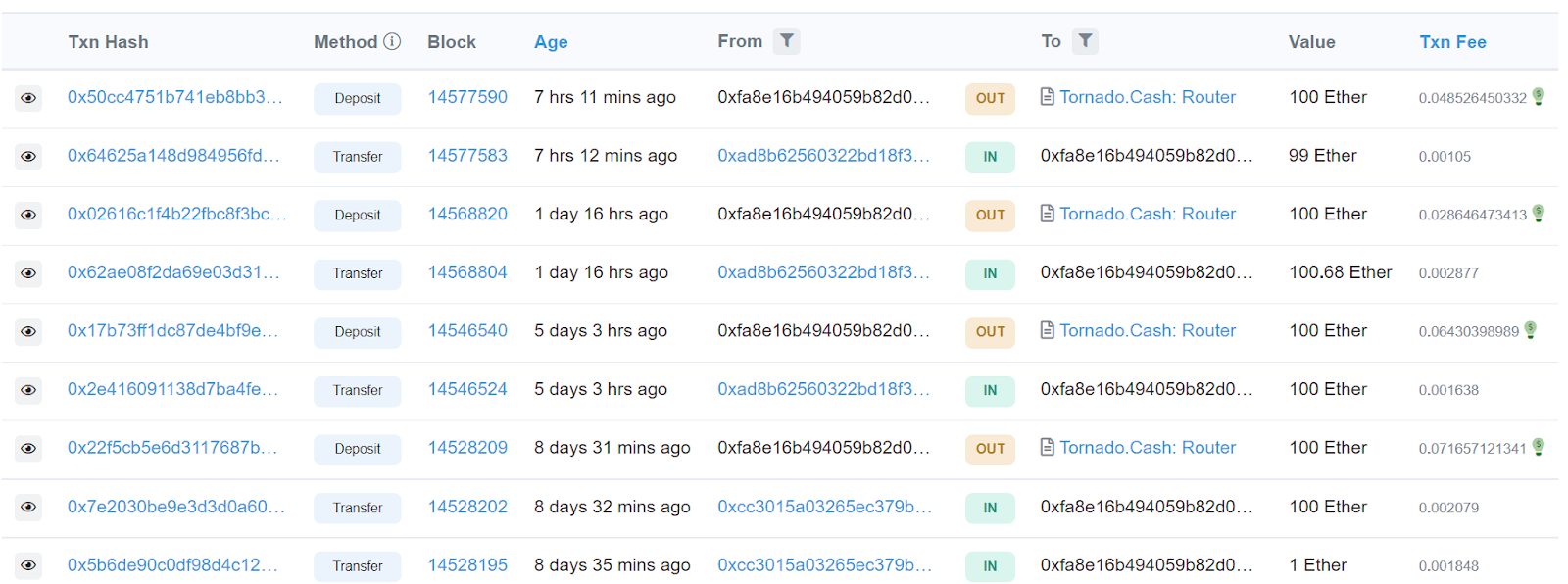
So, this isn’t the “you send 1 eth I’ll send 2 back” scam you used to see, that almost never worked. This works, and it works consistently. After reading this article, hopefully it won’t work on you. I said this last week, but it bears repeating: The hackers’ methods are evolving every single day. If your defense isn’t evolving just as often, you’ll be outclassed before you know it.
If you’d like to view the full thread where I dissected this attack on Twitter & linked the hacker’s addresses, that is available here and is replete with typographical errors & peppered with profanity: so I warned you.

Torrent/seedbox aficionado, decentralist, cultural archivist, fundamental analyst, podcast addict, shitcoin-sifter extraordinaire
Tip Jar
BTC: bc1qahxrp47hpguhx8y8r382dekgca34tlv54aufht
Doge: DJRy9gGSUGeyXfVcZXzKLkBv7RmDLv3MhJ
Share This Article
Join 10,000+ forward thinkers! Get crypto education in your inbox.